I’m wondering if I’m starting to outgrow Tailscale… my wife keeps having networking issues on Android due to Tailscale, the Nvidia Shield kills the Tailscale app randomly, and my parents’ TV doesn’t have a Tailscale app…
I feel like the time is approaching to publicly expose some of my services to the internet…
Any other tips?
Exposing stuff to the internet shouldn’t be that scary… I haven’t had any incident so far in 8 years. Yes, you see plenty of illegitimate access attempts in the logs, but if everything is properly patched, it should be OK.
Exposing services to the internet is a whole other game. Try wireguard first, i never had issues and use it mostly from my tablet.
I am kinda interested in WireGuard, but how does it work with multiple non-PC devices on different networks? Tailscale runs seamlessly on my Arch laptop, but Android, TVs, and streaming sticks have hiccups from time to time.
I have services that I want to share with my non-techie family. If a service stops working, they suck at debugging and fixing the issue on their own.
Tailscale is WireGuard under the hood, if you didn’t know. It’s an overlay network that uses WireGuard to make the actual connections, and has some very clever “stuff” to get the clients actually to connect, even if behind firewalls without needing port forwarding.
Using WireGuard directly basically just changes the app you use, which may or may not help with your issues. But the connecting technology is the exact same.

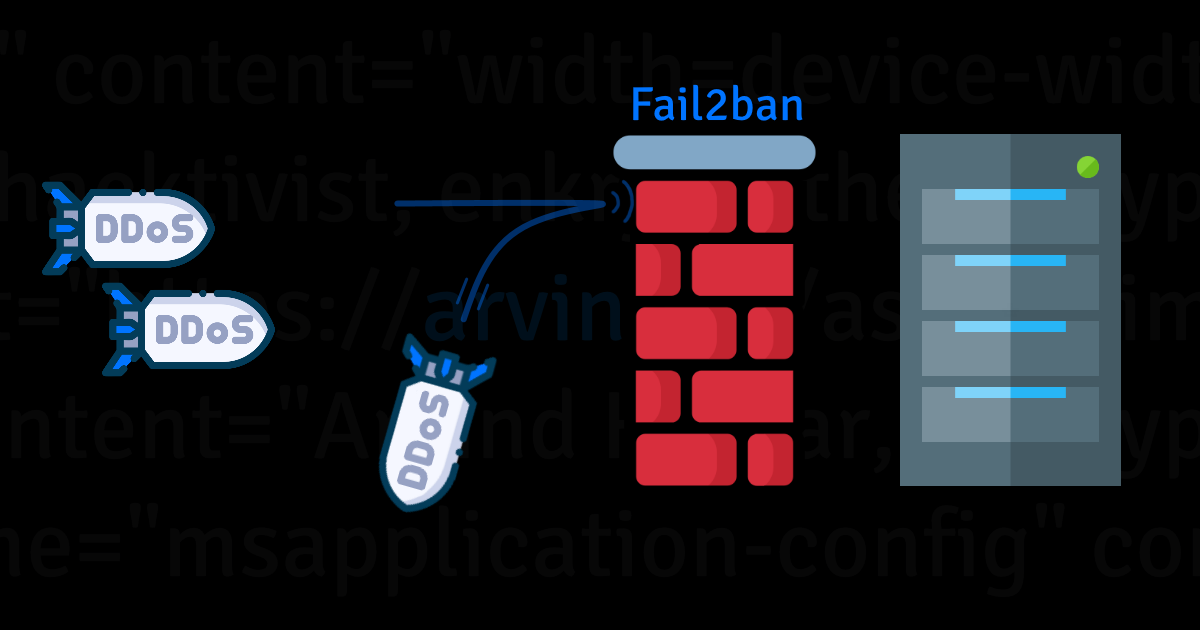
Tried setting this up, caught a few already
I find it hilarious you censored the banned IPs.
Even if they are trying to hack me it’s only polite. Plus on the very remote chance they somehow find this and care they would have slightly more info about me.
Yes, I run many services and website on the public web from my homelab. Harden your server first. Like disabling root ssh login.
Also enable auto updates on your server. Use your router/server to block some counties using geoip (especially if those services are meant for only a couple of people within your county maybe?). You could also use block lists, there any many bad ip lists out there.
Configure rate limits in Nginx.
You also mentioned fail2ban. You can define many rules and actions. Like blocking ips that might go over your previously defined rate limits. Or 4xx action for ips that request a lot of non existing pages (404 errors) .
Also captcha won’t cut it anymore today. Try https://github.com/TecharoHQ/anubis
Of course expose only what you want to expose, so only open ports in your firewall you really want to open. Ideally put everything behind a reverse proxy like Nginx.
Let’s start with all of the things mentioned above. Ping me later if want to know more or have questions.
Harden your server first
Do you have any tutorials or guides on this handy?
Use your router/server to block some counties using geoip
Yeah, definitely all my users are in the same town/region/country as me. So this could be doable.
Configure rate limits in Nginx
Hm, currently using Caddy as my reverse proxy. I guess there’s some module for this.
only open ports in your firewall you really want to open
The only port I need open is 443 for accessing Jellyfin and Immich. I can definitely block 22 from the public internet. And fuck it no automatic redirects from 80 to 443. TLS or bust.
Do you have any tutorials or guides on this handy?
Now that’s a deeeeep rabbit hole. I tend to go overboard on hardening and security, however, one good place to start is installing Lynis and run a scan. Lynis will spit out a rather extensive list of areas you need to harden or adjust and a score for your server. It will also give links where you can go and read up on the specific item in question. Now, not every one of the bullets in the list will apply, but you should give each careful consideration. Lynis is Free and Open Source Software (FOSS).
- Site: https://cisofy.com/lynis/
- Install: apt-get install lynis
- Run:
lynis audit system
I ran a scan just for demonstration purposes so you can see what the end results are. This is just a snippet:
spoiler
* Configure minimum password age in /etc/login.defs [AUTH-9286] https://cisofy.com/lynis/controls/AUTH-9286/ * Configure maximum password age in /etc/login.defs [AUTH-9286] https://cisofy.com/lynis/controls/AUTH-9286/ * Default umask in /etc/login.defs could be more strict like 027 [AUTH-9328] https://cisofy.com/lynis/controls/AUTH-9328/ * To decrease the impact of a full /home file system, place /home on a separate partition [FILE-6310] https://cisofy.com/lynis/controls/FILE-6310/ * To decrease the impact of a full /tmp file system, place /tmp on a separate partition [FILE-6310] https://cisofy.com/lynis/controls/FILE-6310/ * To decrease the impact of a full /var file system, place /var on a separate partition [FILE-6310] https://cisofy.com/lynis/controls/FILE-6310/Be mindful of where you get your hardening tutorials. There are hundreds of thousands out there. I would stick with authoritative sources.
ETA: I would also recommend reading up on Cloudflare Tunnels/ZeroTrust. I know some people are iffy about Cloudflare and I see their points. It’s worth a read in my opinion.
Caddy is also fine.
I wrote a blog about server hardining and you might find it useful: https://blog.melroy.org/2023/server-hardening/