Dedicated wifi for automation allows me to have devices such as Xiaomi Vaccuum, or security camera not phoning home. OpenWRT with good firewall rules completely isolate my “public” containers/VMs from my lan.
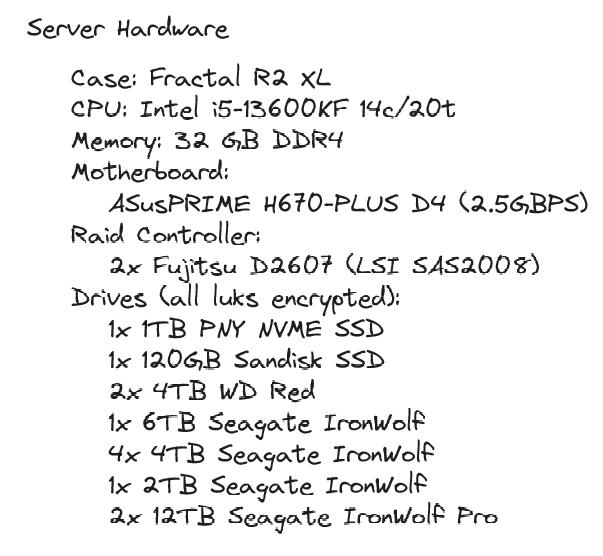
Server was built over time, disk by disk. I’m now aiming to buy only 12TB drives, but I got to sacrifice the first two as parity…
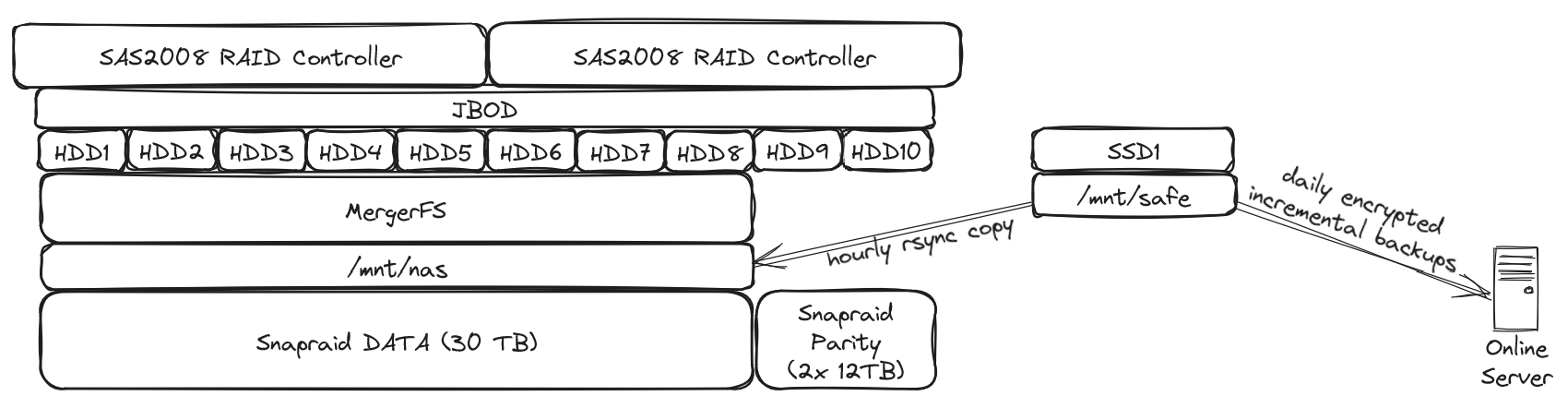
I just love the simplicity of snapraid / mergerfs. Even if I were to loose 3 disks (my setup allows me the loss of 2 disks), I’d only loose data that’s on these disks, not the whole array. I lost one drive once, recovery went well and was relatively easy.
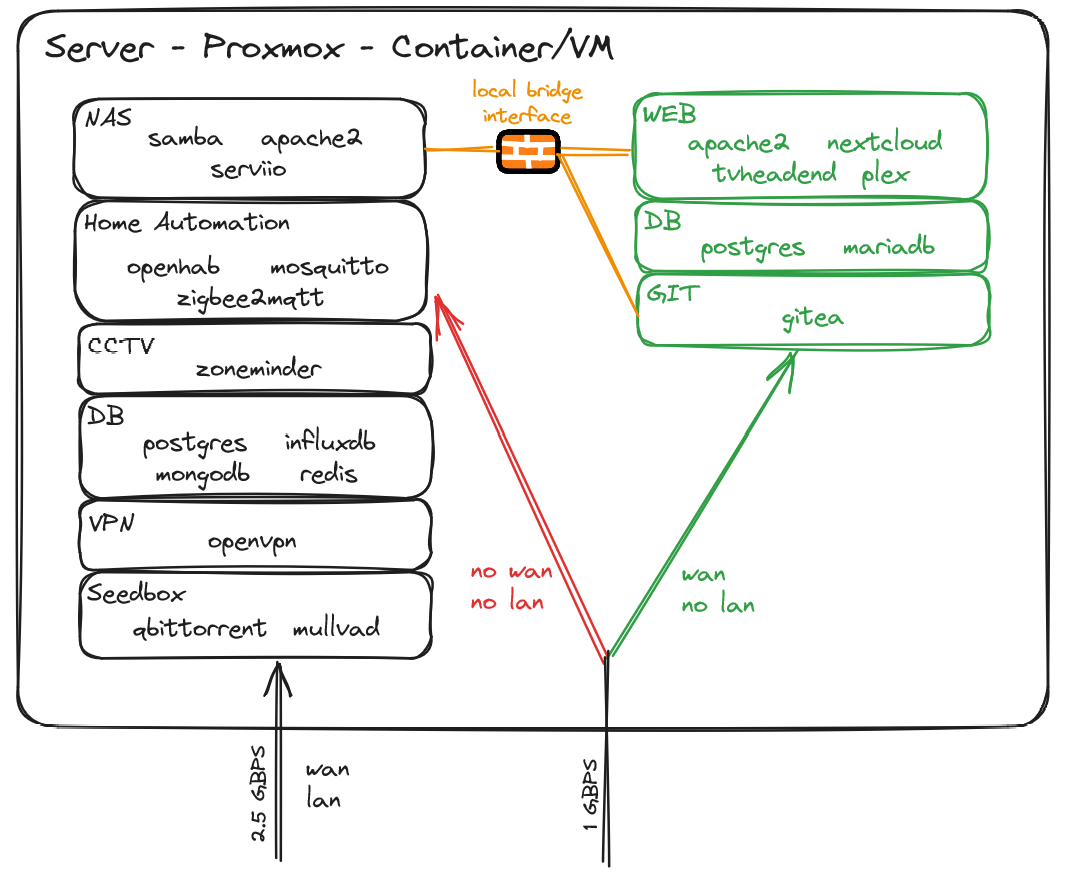
I try to keep things separated and I may be running a bit too many containers/vms, but well, I got resources to spare :)
As an FYI: this set up is vulnerable to ARP spoofing. I personally wouldn’t use any ISP-owned routers other than for NAT.
I’m not well versed in ARP spoofing attack and I’ll dig around, but assuming the attacker gets access to a “public” VM, its only network adapter is linked to the openwrt router that has 3 separated zones (home lan, home automation, dmz). So I don’t think he could have any impact on the lan? No lan traffic is ever going through the openwrt router.
The risk is the ISP Wi-Fi. As long as you’re using WPA with a good long random passkey, the risk is minimal. However, anyone who had access to your Wi-Fi could initiate an ARP spoof (essentially be a man-in-the-middle)
Well, to be honest if someone has access to my Wi-Fi, I’d consider that I’ve already lost. As soon as you’re on my lan, you have access to a ton of things. With this setup I’m not trying to protect against local attacks, but from breaches coming from the internet
Doesn’t need to be the case if you segment your network to protect against ARP.
How would you change his setup to prevent ARP attacks? More network segmentation (clients and servers on separate VLANs) or does OPNsense additional protections I should look into?
Don’t have the Wi-Fi network “upstream” of the LAN. You want the connection between the LAN and Wi-Fi to be through the WAN so you get NAT protection.
Any way you could update/create your own drawing with what you mean? (Bad paint drawings are acceptable!)
I ask because I am curious if I am subject to the same problem. I’m not the most networking savvy so I need the extra help/explanation and maybe the drawing will help others.


